How to Prevent Students From Cheating in Computer-based Exams?
Posted on September 10th, 2021 in Uncategorized | Comments Off on How to Prevent Students From Cheating in Computer-based Exams?
With the development of technology, computers are widely used by various agencies. Nowadays, full computer classrooms are deployed in colleges and universities, many courses can be learned by computer. So, part of the exam will also be conducted on the computer.
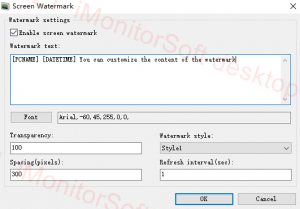
However, technology dose not necessarily bring benefits. According to statistics, some students will cheat to pass the examination, and computers are easier to cheat. This situation will greatly affect the learning atmosphere of students. It is worth mentioning that iMonitor computer monitoring software can help to prevent this situation. It supports remotely monitor all activities of client computers, can view screenshot, remote real-time desktop, keylogger record and etc. If there is a violation, it will be discovered the first time.
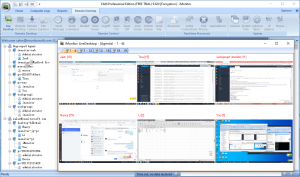
Multi-desktop Real-time Monitoring
iMonitor screen monitoring software supports monitor multiple desktops at the same time, can clearly view all computer activities. It can also select the corresponding client to view the real-time desktop. If the target client is performing an illegal operation, iMonitor can remotely control the operation of the mouse and keyboard of the client to preventing cheating. Such as command sending, restart, shut down, log off, file sending and etc.
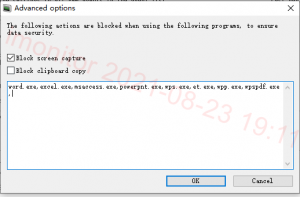
Website Filter Setting
iMonitor supports prohibit the use of the target website, and is able to set the exact period like examination time. This way your students will not be able to find answers on the website. You can open allowed URLs or block unavailable URLs. Students can only operate in limited web pages.
Screenshots Playback
iMonitor records all activities and can be viewed from screenshots. The default screenshots interval is one second, it can be played back like a video. Certainly, you can set the interval yourself, and screenshots supports filter function that can choose the category. If teacher have questions about test results, it is convenient to view all the activities on the computer during the previous test.
The cheating issue will not only affect their grades, but also affect their lives. Similarly, if a student is misjudged as a result, then their attitude towards learning will also changed. In order to let students have a better learning environment, I sincerely recommend you to try iMonitor PC monitoring software.