How to Hierarchically and Centrally Manage Employees?
Posted on November 22nd, 2021 in Uncategorized | Comments Off on How to Hierarchically and Centrally Manage Employees?
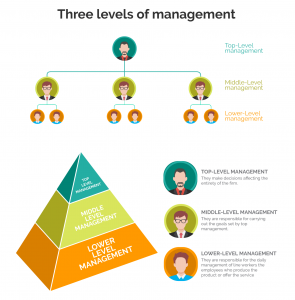
Generally speaking, medium and large enterprises will be divided into different departments according to different responsibilities. Each department has a manager, and the manager will continue to divide the group according to the number of employees in the department.
The purpose of hierarchical management is to make the enterprise work faster and more efficient, eliminating unnecessary works. So, how should an enterprise with multiple departments and levels monitor and manage employees?
iMonitor employee monitoring software can divide different accounts according to different users, and there are three levels of accounts in total.
Administrator user: Have all permissions
Admin is the user created by default, which can add, modify or delete departments, can view the login history of users of other levels set by it. All operations in the agent settings can be performed, such as basic logs setting, file or data security setting, screenshots setting, website or application setting, and keyword filter setting. The most important is only Admin can access the database of server. Database stores all the monitoring record data of every agent, which shows that the monitoring data does not path through the third party, explain that iMonitor computer monitoring software is extremely safe. Admin can be understood as a role set specifically for the boss in the enterprise that has all the control.
Standard user: Unable to view the database, add or delete departments
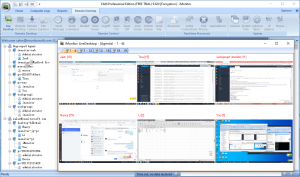
Standard is the user created by Admin, can view the computer logs which including multiple agents compare, global search, and logs summary. For system logs, screenshots playback can show the desktop of agent computer, it records all activities of employee. Keystrokes records all the letters typed, but only the raw keyboard. Standard user can also perform agent settings. A more important function is the reports. Department can create reports to summary the work, network traffic, application, website, files and so on. Through the record reports generated by each department, from different statistical types, you can clearly analyze the work status of each employee or department. In the work quarter summary, can use this function to report and summarize. The standard user account can act as the department manager.
Limited user: can only view logs except keystrokes, have remote desktop, real-time desktop, and access files
Limited user can monitor the working status of the team members, the working hours and busyness of the computer. Though the lower right corner of the console page, can see working efficiency of each agent in the number of keyboard strokes and the percentage of working time. At the same time, double click each time cell, you can see the screenshots corresponding to this time, int which all the employees’ activities are recorded.
iMonitor employee activity monitoring software supports diversified management, the management of the enterprise easier and efficiency.