iMonitor EAM supports windows 8/8.1
Posted on November 12th, 2014 in Uncategorized | Comments Off on iMonitor EAM supports windows 8/8.1
iMonitor
Hello CUSTOMER. How may I help you?
CUSTOMER
still having problems adding a pc to monitor, server is on a win 7 pc and the client i want to monitor is on a win 8 pc, using eam standard ed version 8.52. i have installed the agent.exe locally on the win 8 pc
iMonitor
And?
CUSTOMER
still can’t get the win 8 pc working
iMonitor
Can you see mssys.exe in task manager on the win 8 machine?
CUSTOMER
not in front of that pc right now, what else should i look for so i can take care of it
iMonitor
Firstly please check if you can ping the server from the win 8 machine, then please check firewall and antivirus
Windows start menu -> run -> cmd -> ping server ip address
CUSTOMER
how do i ping the win 7 machine (server) from the win 8 machine (client). i shut off the firewall and antivirus on the win 8 machine
ok i will try the ping, if the mssys.exe is not running, how do i start it.
iMonitor
If not, just reinstall it manually
CUSTOMER
give me five
iMonitor
ok
CUSTOMER
i can successfully ping the server from the client machine
when i try to find the mssys.exe on the win 8 machine ( clinet) i can’t find it in the task manager and i don’t know where it is on the hard drive to run the exe
iMonitor
Did you install it with administrator?
CUSTOMER
yes i believe so, can’t i intall remotely from the server?
iMonitor
Please try to install it manually
CUSTOMER
ok give me five, i will run as admin
great i got it to work thank you
now my next question, on the win 7 client, i want to activate the webcam, how can i do that
iMonitor
The webcam feature has been removed
CUSTOMER
on what version was it removed
iMonitor
from version 8.0
9:42 pm
CUSTOMER
okay thanks
 Business owners usually use
Business owners usually use 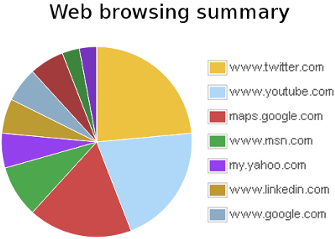
 LOS ANGELES, UNITED STATES (25 / MAR / 2014) .- The first national campaign for cybersecurity to protect minors from sexual predators on the Internet , was launched by United States authorities. Determined to curb the growing number of children falling prey to online sexual predators, representatives of the forces of the local federal joined an organization of the juvenile. The “iGuardian” program was launched by the Immigration and Customs Enforcement (ICE ) Homeland Security Investigations (HSI) with the National Center for Missing and Exploited Children (NCMEC). Last year HSI special agents recorded cases of sexual exploitation by nearly one million hours of child labor. This gave rise to the opening of more than four thousand research. Last week, ICE announced an investigation to an operational scheme of child exploitation in the Darknet Onion Router that involved more than 250 children in the United States and the world. “online sexual exploitation of children has reached epidemic proportions,” stated the director of ICE, Daniel Ragsdale, at an event held in Mission Viejo, California. “There are increasing incidents involving young people insert their explicit images and send them via the Internet, “he added. “Awareness of the risks lurking in cyberspace is critical to help keep children safe,” he said. As part of “iGuardian” authorities visit schools and youth groups in the country to provide children and parents tips on how to avoid falling victim to sexual predators online.
LOS ANGELES, UNITED STATES (25 / MAR / 2014) .- The first national campaign for cybersecurity to protect minors from sexual predators on the Internet , was launched by United States authorities. Determined to curb the growing number of children falling prey to online sexual predators, representatives of the forces of the local federal joined an organization of the juvenile. The “iGuardian” program was launched by the Immigration and Customs Enforcement (ICE ) Homeland Security Investigations (HSI) with the National Center for Missing and Exploited Children (NCMEC). Last year HSI special agents recorded cases of sexual exploitation by nearly one million hours of child labor. This gave rise to the opening of more than four thousand research. Last week, ICE announced an investigation to an operational scheme of child exploitation in the Darknet Onion Router that involved more than 250 children in the United States and the world. “online sexual exploitation of children has reached epidemic proportions,” stated the director of ICE, Daniel Ragsdale, at an event held in Mission Viejo, California. “There are increasing incidents involving young people insert their explicit images and send them via the Internet, “he added. “Awareness of the risks lurking in cyberspace is critical to help keep children safe,” he said. As part of “iGuardian” authorities visit schools and youth groups in the country to provide children and parents tips on how to avoid falling victim to sexual predators online. Ordinary activities in the domestic Internet may be prohibited in the workplace. Who violates the rules is subject to discipline and even dismissal!
Ordinary activities in the domestic Internet may be prohibited in the workplace. Who violates the rules is subject to discipline and even dismissal! Everything employee does on work time – and on company resources. Time spent on frivolous websites can seriously hamper productivity , and visiting questionable websites on PCs now can subject your business to serious legal risks including expensive processes harassment of employees who may be exposed to offensive content.
Everything employee does on work time – and on company resources. Time spent on frivolous websites can seriously hamper productivity , and visiting questionable websites on PCs now can subject your business to serious legal risks including expensive processes harassment of employees who may be exposed to offensive content. Productivity within the company
Productivity within the company The daughter of a colleague, a journalism intern at mining group in Minas Gerais, was to “the street” to share and comment on social networks disparaging facts about the employer during working hours. A similar case occurred in early February when two interns were dismissed by direction of the Senate after criticizing the President of the House, Senator Renan (PMDB-AL), a social network on the internet. I feel sorry for sacked, but earned it, because with the popularity of social networks and media and their impact on the construction and deconstruction of reputations, companies have every right to monitor everything their employees do on their work computer.
The daughter of a colleague, a journalism intern at mining group in Minas Gerais, was to “the street” to share and comment on social networks disparaging facts about the employer during working hours. A similar case occurred in early February when two interns were dismissed by direction of the Senate after criticizing the President of the House, Senator Renan (PMDB-AL), a social network on the internet. I feel sorry for sacked, but earned it, because with the popularity of social networks and media and their impact on the construction and deconstruction of reputations, companies have every right to monitor everything their employees do on their work computer. I saved my son from joining the wrong group
I saved my son from joining the wrong group