File/Data Encryption(Only available in EAM Encryption version)
Select the user on agent list, Click "Home > "Settings" > "Agent Settings" icon to start the Agent Property Setting.
Alternatively, double click an agent in the agent list.
Click the "File/Data Security" tab.
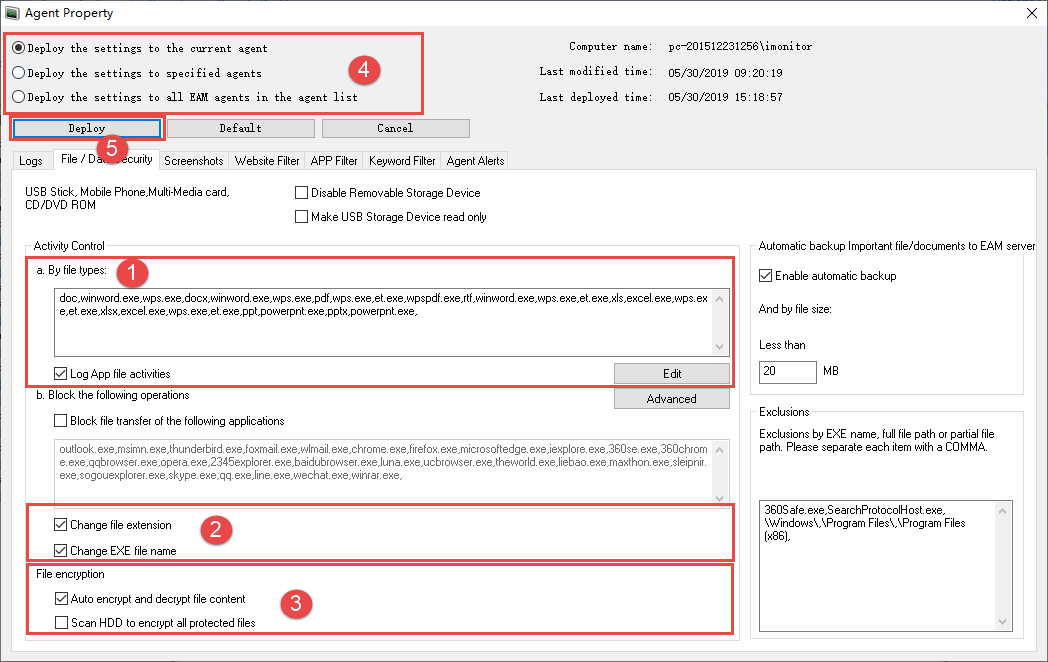
1. Enter the file type extension which you want to encrypt and corresponding application (.exe) in "By File Types" list, use a comma to separate after each term.
For example:
File type extension and single corresponding application EXE: doc,winword.exe,
File type extension and multiple corresponding application EXE: doc,winword.exe,wps.exe
Multiple file type extension and corresponding application EXE: doc,winword.exe,xlsx,excel.exe
(doc and xlsl are file type extension, winword.exe, wps.exe and excel.exe are corresponding application)
2. Tick "Change file extension" and "Change EXE file name".
3. Tick "Auto encrypt and decrypt file content" or Scan HDD to encrypt all protected files.
4. Deploy the settings to the specified agents.
5. Click "Deploy" to finish the settings.
iMonitor EAM Document Encryption Introduction:
For some reasons, some of our customers often encounter the following conditions:
1.When design staff left the company, they may take away the important drawings and documents.
2.The important customer information flowed out after the marketing staff leaves the company.
3.Employees are stealing business opportunities from the company.
4.The company's senior programmers take away the core source code.
5.The important processes of the factory are leaked by employees with ulterior motives.
6.The important documents for external company are being abused, this will take a lot of troubles.
iMonitor EAM Encryption can help you prevent data breaches happen, iMonitor EAM Encryption is a powerful insider threat detection & prevention solution and data security solution. Expect the basic computer & internet activities monitoring, employee tracking, filtering & blocking, reports, and real time alerts features. EAM Encryption has driver layer transparent encryption function, effective defense against data breaches and data leaks. Suitable for large company or the companies who has confidential data need to be protected such as Financial, Research and Development, IT, Design industries.
Functions of iMonitor EAM Encryption:
1. Transparent Encryption: When the files were sent out, it is directly encrypted at the driver layer to guarantee all sent out files are ciphertexts, and the files will be automatically decrypted when the document is normally opened, modified and saved. Both encryption and decryption are automatically finished at the driver layer, without changing the user's work habits, exactly same as before without EAM software installed.
2. Efficient: Mature & stable encryption and decryption algorithm, there will be no delay and stuck.
3. Internal Normal & External Garbled: The encrypted files can be used normally on all computers in the company with EAM client installed, but on the computer without EAM installed or encryption disabled. There will show messy code.
4. Offline Protection: The rules still take effect when the agent and server PC networks are abnormal. For example, when an employee took away the company laptop for business trip, it will also take effect during this period.
5. Full Scan Encryption: Scans the entire hard disk according to the preset file type and encrypts related files.
6. Permanent Encryption: All files in hard disk would be permanently encrypted; Unconventional ways like in DOS system read the files, it would show as cipher text.
More features of iMonitor EAM Encryption